Github: https://github.com/WardPearce/Purplix.io
View our canary: https://purplix.io/c/purplix.io/3ZjhTlZRWv8iqa6sn9yJ3TRiIkVbwITOOlwLjJD36jQ
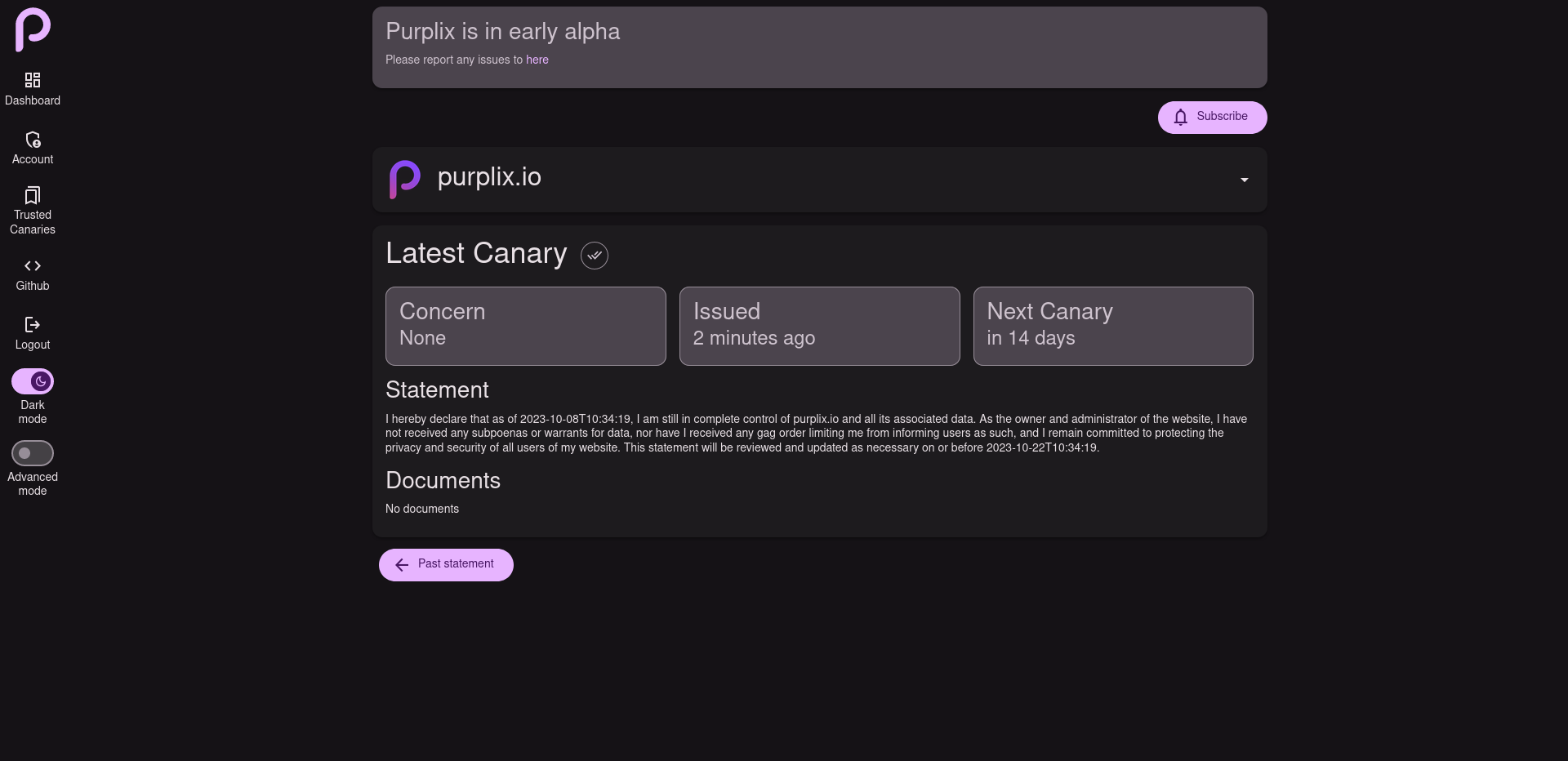
What is Purplix Canary?
Purplix Canary is a free & open source warrant canary tool what helps you to build trust with your users.
It allows you to inform users cryptographically if your site has been compromised, seized or raided by anyone.
How does it work?
Site verification
Purplix uses DNS records to verify the domain the canary is for, giving your users confidence they are trusting the right people.
Canary signatures
Each domain is associated with a unique key pair. The private key is generated locally and securely stored within the owner’s keychain. When a user visits a canary from a specific domain for the first time, their private key is used to sign the public key. This signed version of the public key is then automatically employed for subsequent visits, effectively mitigating man-in-the-middle attacks and ensuring the trustworthiness of canary statements from the respective domain.
Files
Canaries can include signed documents to help users further understand a situation.
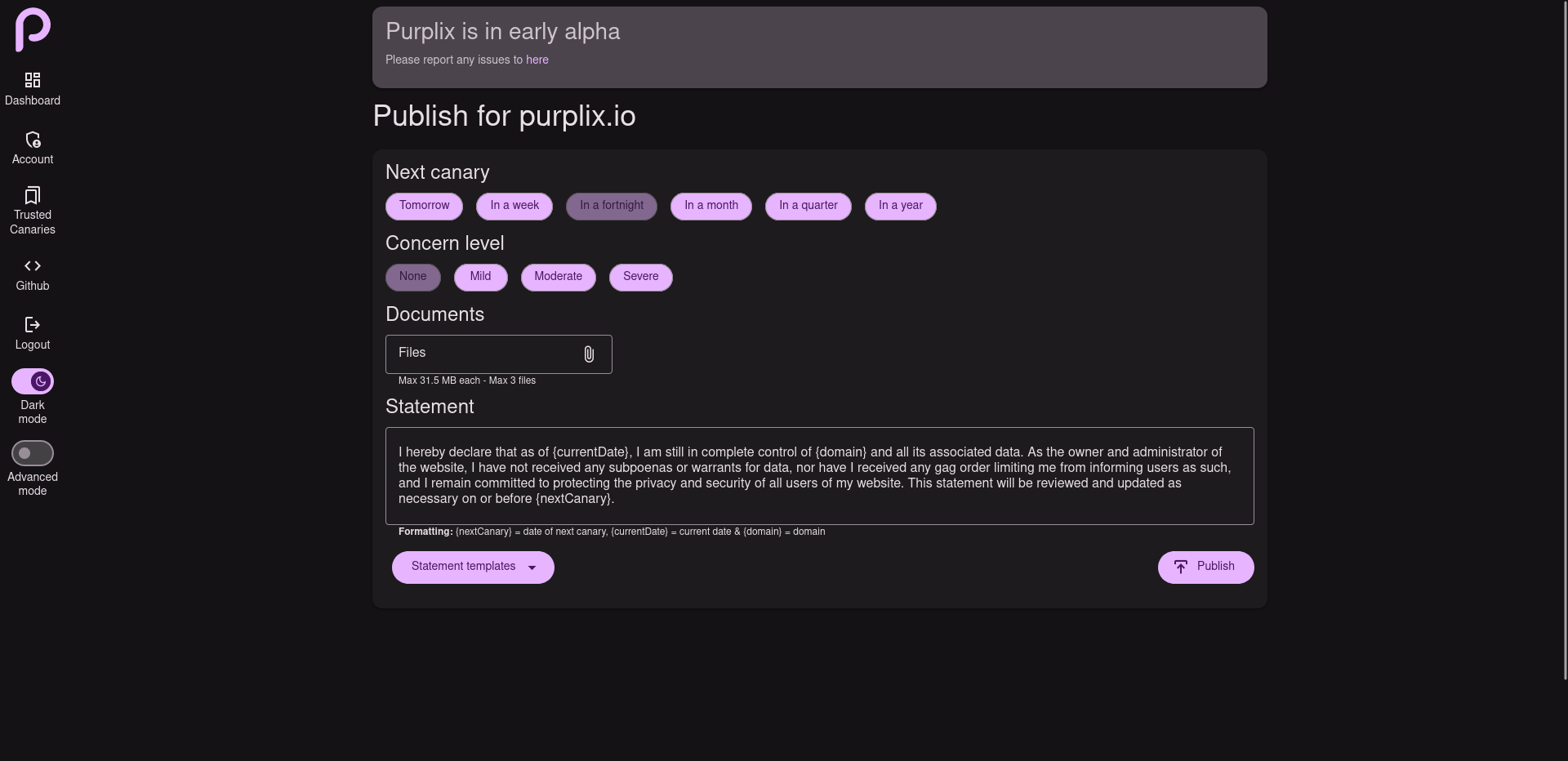
Notifications
Users are automatically notified on the event of a new statement being published.



Shouldn’t there be a notification when a statement isn’t published? Or when the text changes? (Or is that what is meant by a new statement?)
Is the intention to build this into a browser extension?
Love your projects, love the philosophy, great work!
Agreed, should have an alart for missed canaries. Each canary has “statements” you publish new statements to update ur canary. This provides a signed record of passed canaries.
Browser extension or even mobile app could be another aspect of further securing validation. Currently we do store a offline backup for each public key in idb storage & a signed copy if you have a account for further validation if the URL hash has been tampered with.
Thank you for your kind words ❤️❤️